Report: Over 90,000 Users from McGraw Hill’s Third-Party Vendor Exposed in Web Forum

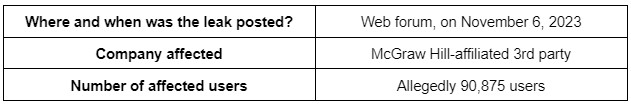
An online forum user shared a database allegedly stolen from a 3rd party associated with McGraw Hill, which the hacker claimed to contain information from 90,875 users.
The vpnMentor research team discovered a web forum post exposing information that was supposedly stolen from a McGraw Hill-affiliated 3rd party. McGraw Hill is an acclaimed educational publishing company in North America. The post was published on November 6, 2023.
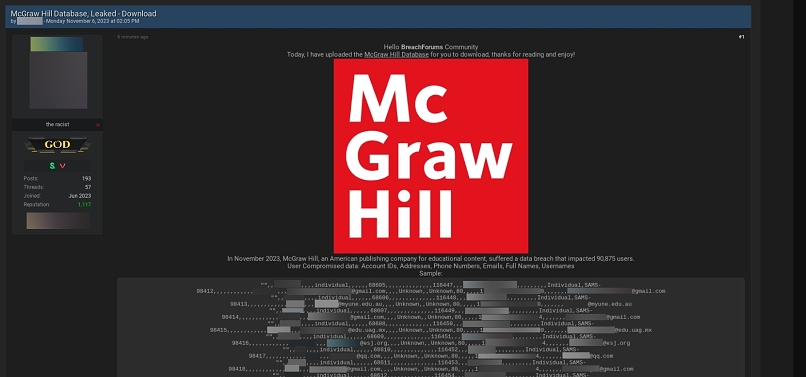 Screenshot of the post exposing McGraw Hill’s users database
Screenshot of the post exposing McGraw Hill’s users database
The hacker posted the data along with a description alleging that 90,875 users were affected. According to the post, among the leaked information are full names, usernames, account IDs, phone numbers, email addresses, and home addresses.
The database was posted behind a paywall; thus, our team couldn't access the link to the full database and only saw the sample shared in the post. Upon the vpnMentor research team’s inspection of the sample data, we confirmed that full names and email addresses are included in the leak. However, account IDs, phone numbers, and addresses were not included in the sample shared — contrary to the hacker’s claims — and we cannot know for certain whether the full database contained such information.
Based on the inconsistencies between the forum post description and the actual information displayed in the sample, the hacker’s assertions could be an overstatement or fake. Nonetheless, our researchers confirmed that the post was made by a forum user who has previously shared several leaked or breached databases that were later proven to be authentic.
Below is a breakdown of our findings:
The vpnMentor team, in its capacity as cybersecurity researchers, contacted McGraw Hill to report the exposed information found on the forum.
The 2022 McGraw Hill Student Database Leak
Back in 2022, the vpnMentor team found and reported a McGraw Hill data leak that affected over 100,000 students.
The exposure came from two misconfigured Amazon Web Services (AWS) S3 buckets belonging to McGraw Hill. The two servers contained over 22 TB of data spread across more than 117 million files. Below is a summary of the 2022 leak:
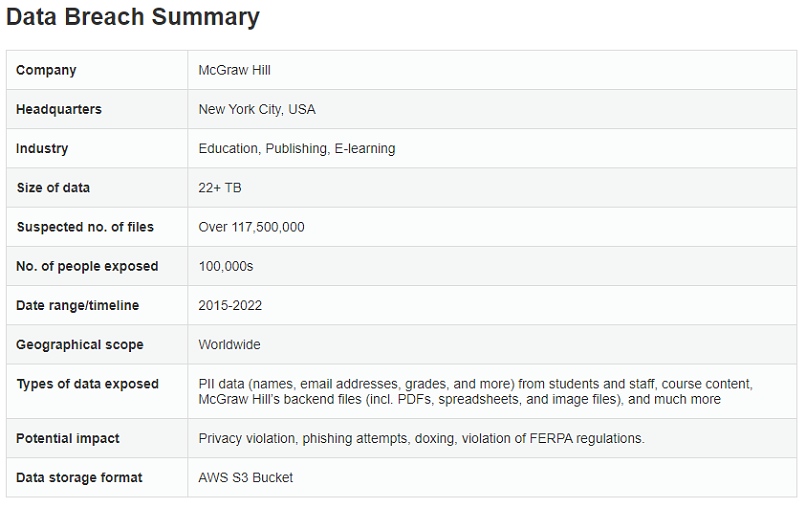 Screenshot of the summary of our report on the 2022 McGraw Hill data leak
Screenshot of the summary of our report on the 2022 McGraw Hill data leak
It is difficult to confirm whether the 2023 leak is related to the 2022 breach we discovered.
Based on our previous report, the format of the database and the lack of supporting documents and auxiliary files in the sample shared by the forum user suggest that the 2023 leak originated from a different component of McGraw Hill’s systems rather than the vulnerability we found in the year prior.
However, there are parallels between the naming convention for the.edu emails in the sample the hacker posted and the report we published. This indicates that the recently leaked data is most likely to be authentic.
Potential Impacts
Hackers can potentially use the exposed PII to commit various types of online fraud or cyberattacks. The PII included in the leak could be used for identity theft, doxing, or phishing attempts.
For instance, cybercriminals could pose as renowned companies or organizations and send the affected individuals emails that may convince them to provide additional sensitive information — such as banking information or social security numbers — or click on malware-carrying links.
What Should You Do if You Think You’re Affected?
If you are a student with an account with McGraw Hill or have otherwise had recent interactions with its online platforms, it is best to get in touch with the company and inquire about the actions it took to secure your data.
It is also recommended to watch for suspicious activity across your online and financial accounts. Check for unusual login or access requests. If you notice any action you do not remember initiating, immediately implement ways to safeguard your information. For instance, you could change your email login credentials.
Why Companies Need Robust Cybersecurity Practices
Data breaches can severely impact businesses and organizations. When malicious actors get their hands on people’s personally identifiable information (PII), those affected can be victimized by fraud, identity theft, and various other cyber crimes. This can be disastrous not only for the affected individuals but also for a company’s finances and reputation.
In addition, publicly leaked data cannot be recovered. The company may patch the security vulnerability, but any sensitive information that malicious actors have acquired can no longer be secured. There is no way to retrieve the data from the hackers or prevent them from sharing and continually exploiting it.
To prevent instances similar to the McGraw Hill leak, companies may take the following steps to secure their servers:
- Ensure proper access rules to prevent unauthorized access to sensitive information.
- Establish guidelines for staff to follow when processing confidential files.
- Clearly communicate privacy and disclosure policies to all stakeholders.
- Implement and regularly update third-party security software and cloud encryption.
- Create incident response plans and set regular testing schedules to check their effectiveness in mitigating damage during potential leaks and breaches.
vpnMentor published the results of an experiment wherein we created a honeypot to see how quickly external actors can find and access a misconfigured database.
We set up misconfigured AWS S3 buckets, which outside actors accessed within 20 days. The fake data we placed in the servers were accessed over 700,000 times in 14 months. No outside actor ever contacted us about the breach. Our honeypot research report details the methodology and results of the experiment, as well as our analyses.
It is important to note that AWS and the other cloud storage platforms used in the experiment are not to blame for the misconfigured servers. Our team had to manually ignore several misconfiguration warnings from Amazon and change the default settings to leave our AWS S3 bucket vulnerable. This shows that proper server configuration is almost always under the control of users.
What Are Clearweb Leaks and Why Should You Care?
Hackers use all corners of the internet to share information, organize cyberattacks, and talk about data breaches. Some of hackers’ preferred channels are clearweb forums. These are online networks that allow users to post information about breaches and leaks. They offer anonymity to their members and have features like paywalling for users who choose to require payment from those who wish to access their shared data.
Clearweb forums are also easier to navigate. Unlike darknets, these open forums do not require users to have technical savvy to access the platforms and post databases. However, this means that cyberattackers can share stolen information faster, putting more individuals at risk of getting their PII and other sensitive data exposed. Also, since users can effortlessly find and browse these forums, more people can acquire the breached or leaked information.
Our cybersecurity researchers scour popular data breach forums on the clearweb to find the latest cyberattacks, leaks, and breaches.
By reporting on these incidents, we aim to proactively inform potentially affected parties earlier so that they can act quickly to protect their data. Our disclosures are rooted in meticulous research and are intended solely for informational and preventive purposes. They should not be interpreted as accusatory or indicative of negligence on the part of any entity.

